Data Location Awareness
Technical Details -
DataLenz runs on IBM Z mainframes with supported releases of z/OS.
Installation of the DataLenz z/OS agent is simple and straight-forward, along with limited network configuration.
DataLenz supports all z/OS data types.
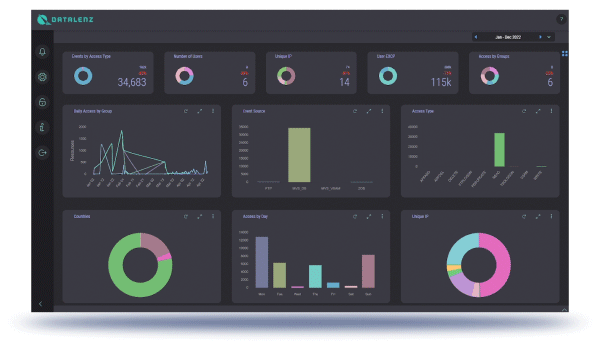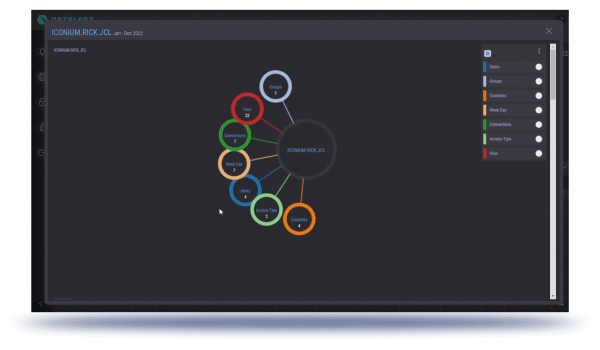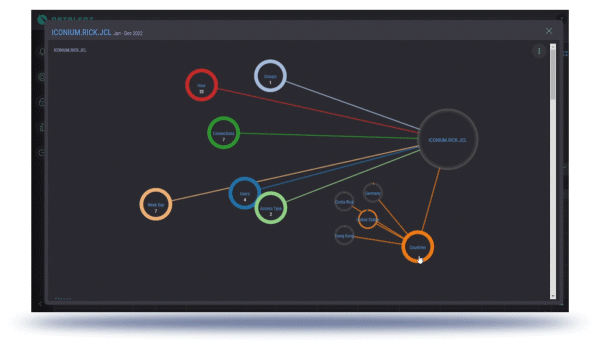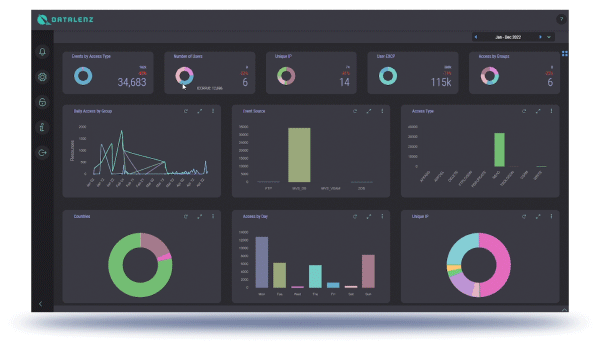
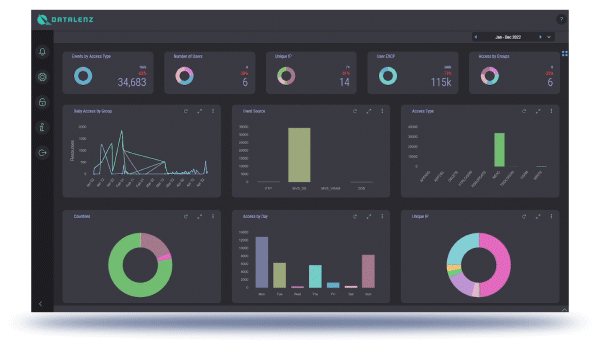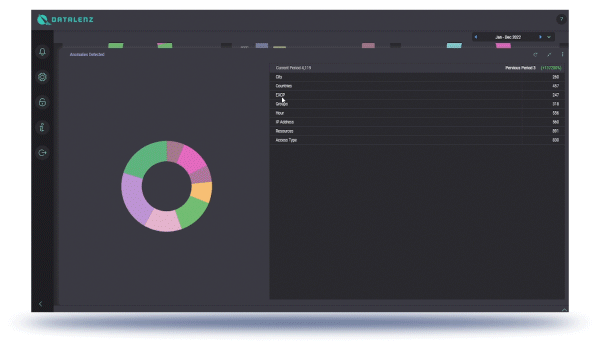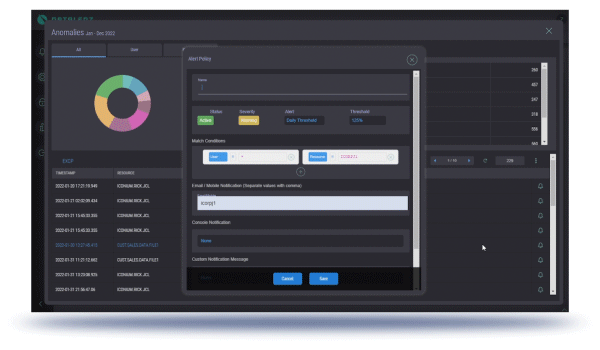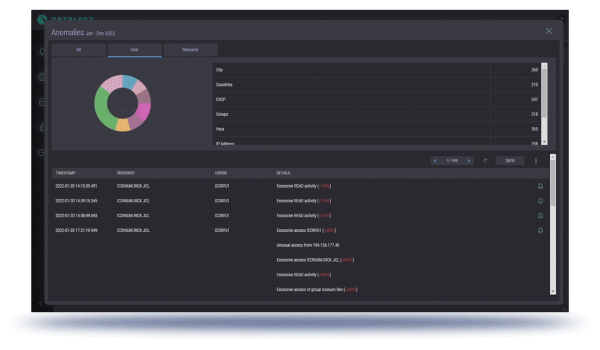
Data access start and end events are recorded for specified datasets, and kept in mainframe-based logs, accessible for reporting and real-time monitoring and alerting through the graphical interface.
The administrative and reporting interface runs as a workstation client, with secure access to your IBM Z mainframes running the DataLenz agent.
The patent pending DataLenz technology tracks the location of your employees, partners, contractors, and rogue actors, with the actual IP address of the device they are using, even if they are going through VPN or using NAT.
What is Geolocation?
This is where Geolocation comes in: knowing where users are physically located when accessing your corporate data and applications. By having a clear picture of where a given device is geographically located, regardless of intermediary steps such as VPNs, firewalls, and network address translation, a clear picture can be established of every device that is operating out-of-bounds geographically and accessing sensitive functionality and data.
Because of the need to cut across all the above-listed layers of security to establish this information, it has been a concept that took a long time to arrive, but it has been needed since the first mainframe TCP/IP stack was turned on in the 1990s.
Of course, a proper Geolocation solution requires the tools, instrumentation, monitoring, alerting, and sophisticated querying and reporting to play a dynamic and active role in protecting your organization from inappropriate access from untrusted locations. So, it must have a clear picture of the actual physical location of every user device and workstation accessing your IBM Z data and applications. But it must go beyond that advanced instrumentation to include:
Real-time monitoring of access to all sensitive data and applications.
Real-time alerting whenever an inappropriate access is detected.
A flexible, powerful, and easy-to-understand-and-use interface that literally gives a clear map-based picture of the nature, location, and number of accesses, with the ability to filter and drill-down to just specific actors, applications, and data.
The ability to flexibly and dynamically configure monitoring criteria, and the ability to give that access in a limited manner to monitoring and security personnel with a narrower scope.
Reporting functionality that can be run regularly or on-demand and specify any, all, and only the relevant criteria for the intended recipients of specific reports.
Only when an environment has such a system configured and running is it possible to begin to fine-tune access controls to ensure that employees, contractors, partners, and even rogue actors, are caught in the act and appropriate countermeasures are immediately taken.
Would you like to know more about DataLenz? Send us a message.